

Your employees are often your first and last line of defense, and criminals know this. Many cyber attacks can be stopped immediately, with a keen eye and awareness of threat actors' strategies and tools. A simulated attack usually leaves a stronger impression than any information security training, because no one wants to be fooled or taken advantage of. Doing this respectfully and educating makes your employees security ambassadors and strengthens your organization‘s security posture.
All cyber security reports show that attacks on people, and specifically phishing, remain the number one technique for initial access.
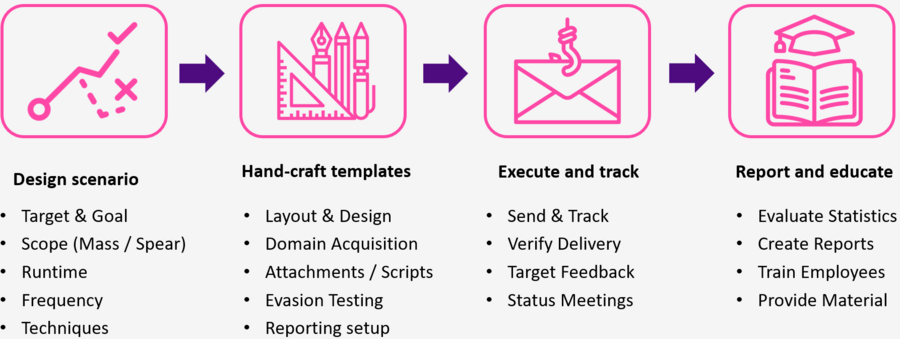
Targeted and customized phishing campaigns help your employees to identify and avoid real threats.

Sometimes it’s easier to just walk in – let’s make sure it doesn’t happen to you
A card reader that can be tricked, an unprotected network port, or even an employee that opens the doors to your server room in goodwill – these are typical encounters when we test our clients' physical security. Together, we identify possible weak spots and check whether your employees become suspicious or willingly open doors when a stranger approaches them and asks to be let in with a believable reason.
And of course, we never forget our 'get out of jail' card.
Get in touch

Tricking your employees into giving away sensitive information that can be used for attacks is a common practice for advanced threat actors.
Whether it is about the technology you use or about processes and how your organization works, information can make the difference between a failed and a successful cyber attack.
We help to sharpen your organization's security skills with customized social engineering exercises. Standalone, or as a basis for and combined with a penetration test.
Get in touch

Curiosity killed the cat – learning the hard way that you should have been suspicious leaves an impression
Plugging in a malicious USB stick on your IT equipment can be the beginning of the end. But we can help you prepare for this. We distribute specially prepared USB sticks in and around your premises. When they are plugged in by an unsuspecting employee, they automatically execute scripts that check the computers' ID and report back to a cloud portal that they have been plugged in. A customized on-screen message will let your employees know what happened and what to do with the stick.
Get in touch