

Cybersecurity Insights by Markus Seme, from June 23, 2025
Iran and Israel have been officially at war since last Friday. Under global scrutiny, thousands of ballistic missiles and drones have already been launched. While images of attacks, defense systems and burning cities dominate the headlines, a second, less visible conflict is taking place in parallel - just as dangerous and potentially just as far-reaching: the digital war in cyberspace.
In recent days, there have been a number of targeted cyber attacks on both sides, which are not limited to website defacements or propaganda campaigns, but are increasingly targeting critical infrastructure and industrial control systems (OT systems).
For example, hacker groups with close ties to Iran claimed to have compromised the Israeli early warning system Tzofar - a system used to alert civilians of incoming missile attacks. Israeli radio stations, government websites and telecommunications services were also victims of coordinated DDoS attacks. Meanwhile, the pro-Israeli group Predatory Sparrow claimed responsibility for a massive cyber attack on the Iranian state bank Bank Sepah, in which systems were paralyzed and data destroyed. This was followed shortly afterwards by another attack on the Iranian crypto exchange Nobitex, and announced plans to disclose internal data and source code.
What all these incidents have in common is the focus on networked OT and IoT systems: systems that control physical processes in industry, utilities and infrastructure - from SCADA systems to PLC controllers, cameras and payment systems through to router and gateway technology.
At the heart of many of these attacks is a malware called IOCONTROL. It was first documented around two years ago - and many of the technical analyses known today come from the security company Claroty, which specializes in OT security. Claroty was not only able to decipher the architecture and communication structure of the malware, but also prove its connection to earlier attacks on control systems. Claroty is one of the leading companies in the field of OT security - with technologies that are among the most effective security solutions for industrial networks worldwide. We have also been working closely with Claroty for a long time and value their expertise and solutions in numerous OT projects.
The malware itself is specifically targeted at Unix-based IoT and OT platforms and uses a modular framework that can be deployed on various devices across platforms. It nests permanently in the systems, survives reboots and is automatically executed at system startup. Exactly how IOCONTROL gets onto the systems is not yet fully understood. However, it is likely that many target systems have already been infiltrated in advance over a longer period of time - using known vulnerabilities, default passwords and publicly accessible remote access. In particular, poorly secured or never hardened systems that are or were directly connected to the Internet offer an easy gateway.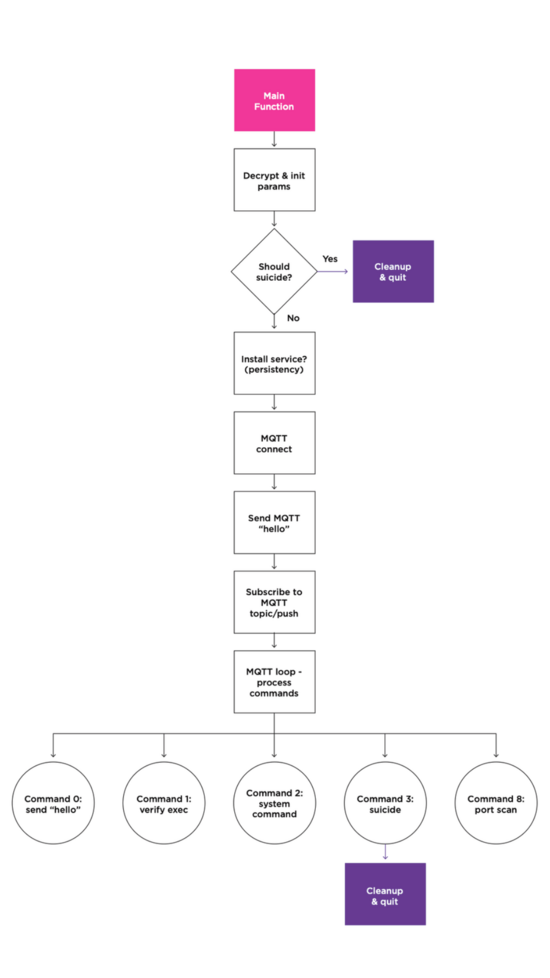
One particularly concerning detail: the malware communicates with the command and control server via protocols such as MQTT, which are widespread in OT environments but difficult to monitor - encrypted and disguised as machine communication. Even the initial DNS request to establish contact is encrypted - using DNS-over-HTTPS (DoH), as offered by Cloudflare, for example. This combination not only makes detection more difficult, but also renders traditional security monitoring virtually ineffective.
The attacks clearly bear the hallmarks of state-supported actors. On the Iranian side, groups such as APT34 (OilRig) or Cyber Av3ngers operate , which specifically target OT systems. On the Israeli side, the Predatory Sparrow group is portrayed as an independent hacker collective, but experts consider it to be presumably supported or coordinated by the Israeli elite unit Unit 8200.
Unit 8200 is one of the largest and most powerful units within the Israel Defense Forces (IDF). It is responsible for electronic reconnaissance, cyber operations and digital warfare. Thousands of highly specialized technicians, cryptographers and data analysts work in this unit - many of whom go on to shape Israel's start-up and cybersecurity landscape. Unit 8200's capabilities and resources are considered a global benchmark for military cyber expertise.
Although most attacks to date have focused on Israeli and American targets, European companies - especially those with networked OT environments - should not be lulled into a false sense of security. The tools and techniques used could be (or already are) used in a similar way for cybercrime, sabotage or collateral damage in other regions.
 Markus Seme is Managing Director of BearingPoint Austria and part of the management of BearingPoint Products. With over 15 years of experience at BearingPoint, his focus is on cybersecurity, digital resilience and innovative security solutions. He supports companies in arming themselves against current and future cyber threats.
Markus Seme is Managing Director of BearingPoint Austria and part of the management of BearingPoint Products. With over 15 years of experience at BearingPoint, his focus is on cybersecurity, digital resilience and innovative security solutions. He supports companies in arming themselves against current and future cyber threats.